We use cookies and similar technologies to recognize your repeat visits and preferences, to measure the effectiveness of campaigns, and improve our websites. For settings and more information about cookies, view our Cookie Policy. By clicking “I accept” on this banner or using our site, you consent to the use of cookies.
I Accept
This article contains:
Ransomware, malicious software designed to block access to a computer system until a sum of money is paid, and the use of exploit kits to distribute it, are adding new challenges to threat detection and protection. And now Angler, an exploit kit, which has been a known Internet threat since 2013, is being used to distribute ransomware. With the sole intent of installing ransomware on victim’s machines.
Our AVG Web Threats team is tracking these widespread ransomware attacks being delivered by the Angler crimeware exploit kit.
The use of exploit kits to distribute ransomware is a new trend – one that could cause widespread ransomware distribution. Exploit kits are software packages readily available for sale and are used by malicious operators to easily create malware that performs a wide variety of malicious functions. The malware is installed on hacked web servers and attacks the machines of visitors to web sites, in many instances, without their knowledge.
There is a common misperception that web users are only at risk if they browse risky sites, however, hacked sites are often brand names and appear safe. Small business sites in particular can be prime targets because they have less security and their visitors typically know the company and trust their brand.
The malware on these sites seeks out vulnerabilities in commonly used tools that improve website experiences, such as Flash, Silverlight and other software that employs Java and PDF-format files. The malware then runs malicious code on the visitors’ machine to install ransomware, backdoors and Spybot clients.
Our AVG Web Threats team has researched a particular instance of a Java exploit commonly found in association with Angler. This threat is detected by AVG, which we’ve been detecting since January. AVG customers who participate in anonymous threat sharing reported 6,123 hacked domains serving Angler in January, 8,260 in February and 4,412 in March.
Angler ransomware installs
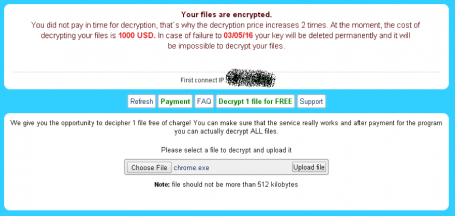
TeslaCrypt is the most common type of ransomware installation currently that’s associated with Angler, according to our AVG Web Threats team analysis of this threat. TeslaCrypt encrypts users’ files, including writeable shares, and messages the user to extort payment for recovering the encrypted data. Paying the ransom to unlock files typically does not result in the recovery of the files.
Below are screen shot examples of ransomware attacks that attempt to extort $1,000 USD, payable through the untraceable currency of bitcoins.
Backdoor installs
Our AVG Web Threats team track the Angler-infected host machines have also tracked incidences of downloading malware known as backdoor malcode (commonly Bedep). Backdoor, or Bedep, can snatch passwords and personal confidential data from visitors’ machines.
Protecting your desktop
AVG recommends that consumers and businesses take the following preventive measures:
- Frequently backup data and important files; do not leave the backup device connected to the machine
- Ensure that security software, such as AVG, is up to date
- Ensure that Windows updates are downloaded and installed; doing this automatically is recommended.
- Update browsers and ensure you are using the latest versions available
Protecting web servers
Malicious code from the Angler exploit kit is initially installed on the web pages of vulnerable servers. For businesses, standard security precautions and monitoring are the basic defense. Researchers find a large number of Angler injections on WordPress and Apache servers - these should be given an extra measure of scrutiny.
- Ensure all Operating System patches and updates are applied quickly
- Regularly review and assess the state of 3rd party software running on the server. For example, vulnerabilities in packages like WordPress are particularly important, as these are common attack vectors
- Consider removing site content and 3rd party software that is out of date or not being used
- Keep backups of websites in a safe place (not on a shared directory); offsite backups are best
- Monitor web pages for unexpected and unauthorized changes
- Keep antivirus and other security software, such as AVG, updated
- Consider using intrusion detection applications, such as AVG
Our AVG Web Threats team continue to monitor and track threats such as Angler, so that we can deliver the security you need to keep your devices and businesses safe.
